Microsoft works with researchers to detect and protect against new RDP exploits | Microsoft Security Blog

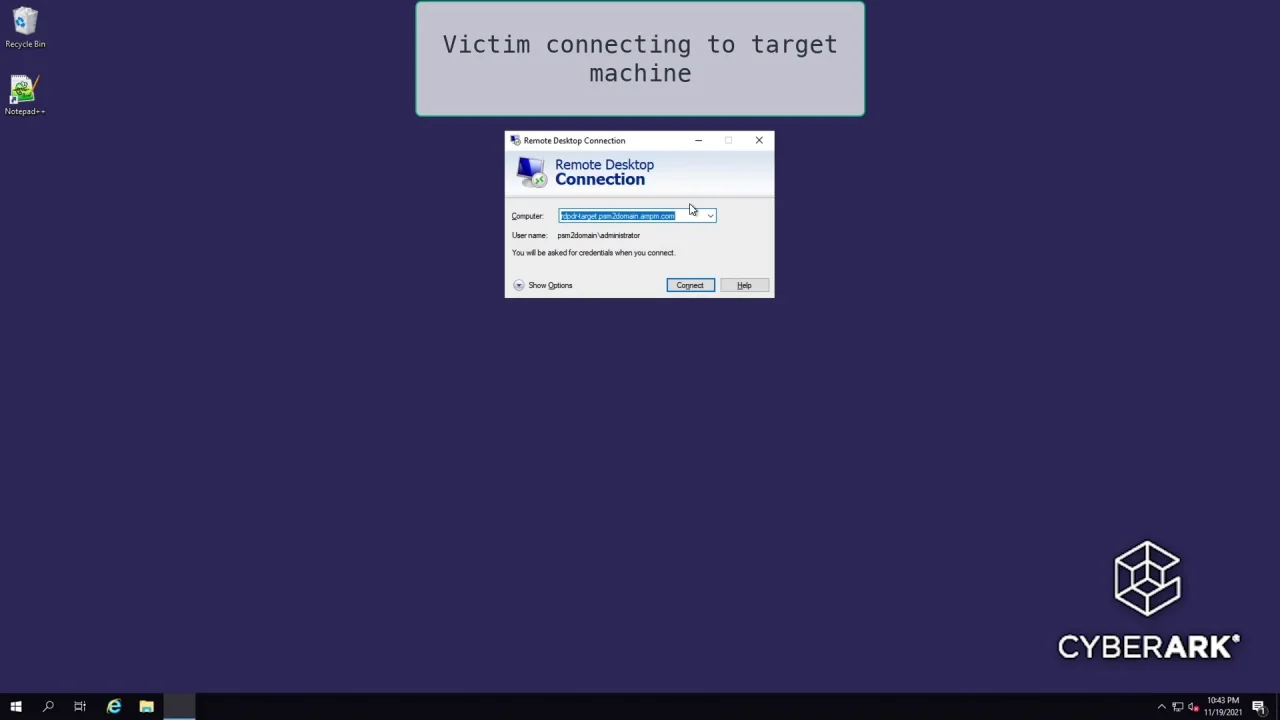
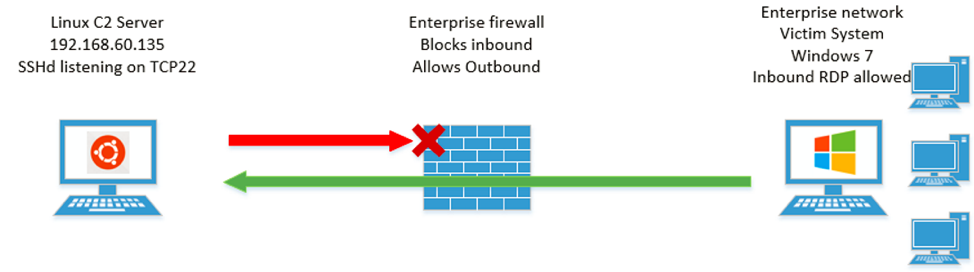
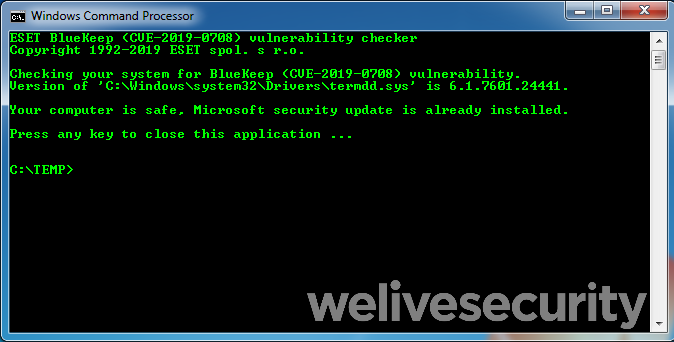
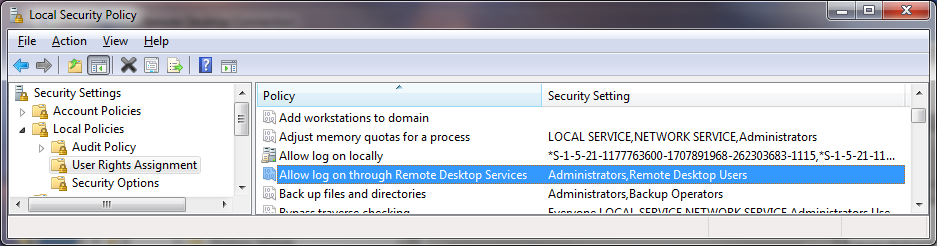
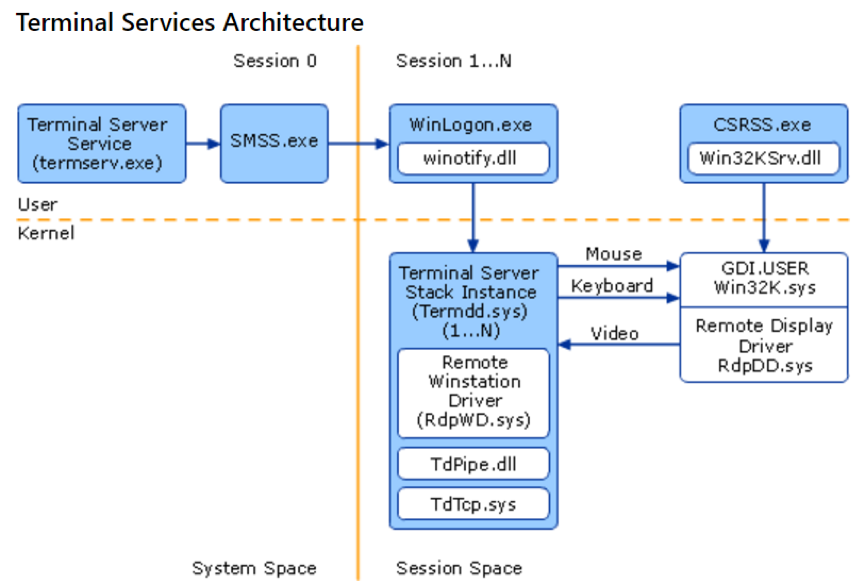
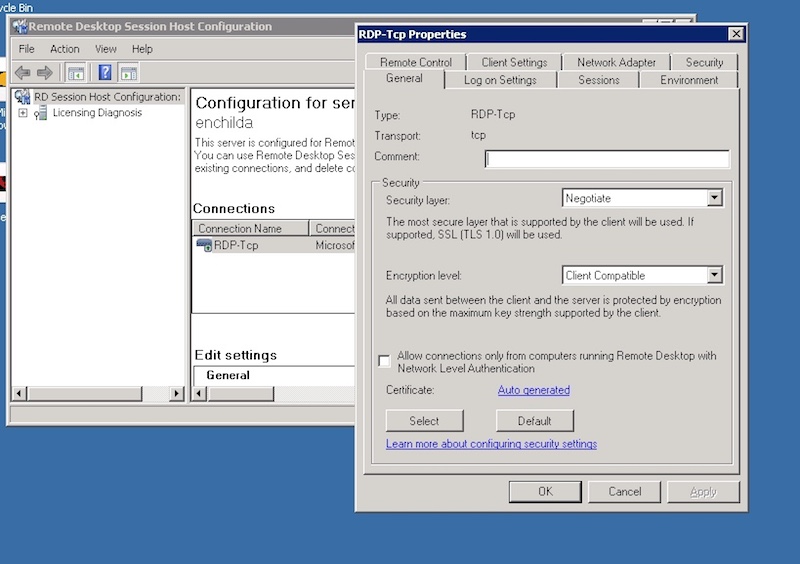
Attack Chain Series: Remote Access Service Compromise Part 1 — RDS | by Vartai Security | Vartai Security | Medium

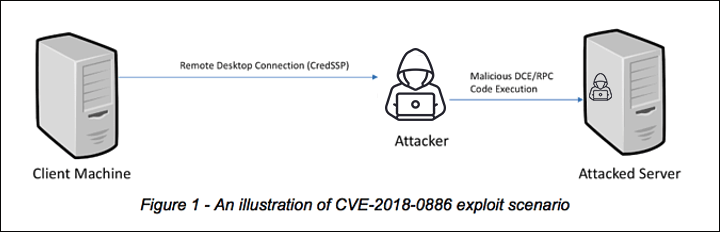
NSA Cybersecurity Advisory: Patch Remote Desktop Services on Legacy Versions of Windows > National Security Agency/Central Security Service > Article

Attack Chain Series: Remote Access Service Compromise Part 1 — RDS | by Vartai Security | Vartai Security | Medium